A recent story by the Washington Post revealed that Facebook’s algorithms had censored the United States’ Declaration of Independence, flagging it for alleged “hate speech”.
The post was removed from the social network because it contained the phrase “merciless Indian Savages.” The post was later restored, but not before the incident began to be discussed around the world. There were several other similar incidents – for example, a famous photo of a Vietnamese girl crying during a US bombing, or posts showing violence against Palestine activists, and so on.
Some experts argue that this absurd situation is a result of a mixed system combining artificial intelligence and human resources… but the real problem goes even deeper – it is a part of how social networks function, and whose interests they have come to serve.
As in politics, we see only the tip of the iceberg. Most polls, games and applications collect personal data about us, facilitating narcissism and then exploiting the resulting behavioural patterns.The more we become involved in this new online kingdom, the more opportunities there are to draw our attention to some of the disturbing topics emerging from its ubiquity in contemporary society.
There have been many studies done on how the US Deep State manipulates social networks. It is well known that the CIA used Google and Twitter as a propaganda tool and an instrument to steer public opinion.

The military and social networks: facts of international intervention
While the Internet itself is a creation of the Pentagon, the opportunities provided by social networks allow the government to conduct new psychological and information warfare at an unprecedented level. Thus, the Pentagon’s report “the Information Operations Roadmap,” published in 2003, explicitly mentions participating in projects such as public relations specialists, psychologists and computer network specialists.
It is time to admit that military projects are implemented with funds and goals of the Ministry of Defense, and paid mediators can be journalists, writers, activists. Given that the central command is responsible for the regions of Central Asia, the Middle East and East Africa, we can talk about direct intervention in the affairs of other countries.
One example was the scandal in 2012, when an investigation revealed that a Pentagon-recruited contractor who created the fake accounts had $4 million in unpaid federal taxes. Another example is the Pentagon’s sponsoring of PR agencies for secret propaganda campaigna in Iraq (including a fake al-Qaeda video aimed to “prove” terrorist activity in the country).
Another interesting project was the launch of US military intelligence’s Military Memetics in 2006, a group of specialists that developed memes to create memes with specific political ideas, and then spread them on social networks through their agents. Today, Memetic Warfare is no longer just a project, but a reality in the battle for narratives, ideas and social control on the web. This has become an important strategy within the Western community, especially NATO.
The Pentagon’s interests have only increased since– for example, in 2011, the Department of Advanced Research Projects of the United States Department of Defense (DARPA) presented its own program “Social Media in Strategic Communication” (SMISC) for conducting propaganda campaigns in social networks. Now DARPA is actively involved in projects related to artificial intelligence (more than 20 programs) and cybersecurity (more than 60).
The US military is especially active on Facebook and Twitter, which have become glorified propaganda and counter-propaganda platforms. Similar tasks were set in the course of the operation “Trident Juncture”, organized by NATO. The United States also holds annual exercises called “Cyber Guard” and “Cyber-flag” which deal with information warfare.
Coalition of state and non-state actors
Some of the reports show how well a state can use non-state actors against another government.
In recent years, the US Army continues to actively engage in this area. For example, in 2016, the US Army Military College issued a “Strategic Cyberspace Operations guide,” which states that “Obviously, cyberspace has become pervasive in our lives, not just in the national defense arena, but also through social media, publishing and broadcasting, expressions of human rights, and expansion of international commerce, both through online markets and online commercial techniques.” It openly states that “non-state entities can provide cover for state-based operators.”
In 2018, the Joint Chiefs of Staff issued the report “Cyberspace Operations,” where the following is written: “The cyber-persona layer consists of network or IT user accounts, whether human or automated, and their relationships to one another. Cyber-personas may relate directly to an actual person or entity, incorporating some personal or organizational data (e.g., e-mail and IP addresses, Web pages, phone numbers, Web forum log-ins, or financial account passwords). One individual may create and maintain multiple cyber-personas through use of multiple identifiers in cyberspace, such as separate work and personal e- mail addresses, and different identities on different Web forums, chat rooms, and social networking sites, which may vary in the degree to which they are factually accurate. Conversely, a single cyber-persona can have multiple users, such as multiple hackers using the same malicious software (malware) control alias, multiple extremists using a single bank account, or all members of the same organization using the same e-mail address.”
Non-military wars
Experts are increasingly talking about “non military wars” and new technologies aimed at ideological and economic rivals, as well as threats to personal data.
Influence technologies on social networks are well studied by organizations such as Hezbollah in Lebanon, Kurdish groups in Turkey and Syria, Hamas in Palestine, as well as many separatist movements around the world. Groups successfully use social media platforms for attracting new members (through target groups), organizing crowdfunding and manipulating public opinion.
If the military and the militants successfully used social networks for their own purposes, why shouldn’t politicians do the same?
The United States’ Cyber Strategies
Information technology was introduced into US policy and strategy during World War II, at the time it was called Public Diplomacy 1.0. Cinema, radio and newspapers (as well as television a few years later) were the main tools of the United States Information Agency (USIA).
Under Obama’s presidency, the Internet and especially Facebook and Twitter have become an important element of external strategy. Cyber specialists were in great demand in various pro-American projects under the guise of “human rights.” At the same time, the online platform Movements.org was created, and the first constituent congress of its participants was held in 2008 in New York. US State Department employees, members of the influential Council on Foreign Relations, former employees of the US National Security Council, advisers to the Department of Homeland Security and RAND employees met with representatives from AT & T, Google, Facebook, NBC, ABC, CBS, CNN, MSNBC, MTV and other companies to launch a new project to promote global democracy.
The list of partners includes many groups and organizations that were involved in color revolutions and attempts to destabilize national governments in different countries.
Another related organization is Cyber Dissidents, founded in the same 2008 year. This initiative is sponsored by the CIA Freedom House. It is a kind of umbrella structure for activists from different countries in which the United States sees “problems with freedom of thought.” The goal of training activists by US non-governmental organizations is to destabilize America’s political enemies in the name of freedom.
The Modern Cybersecurity Program
The latest related military project was presented by the National Council on Science and Technology (NSTC, which is subordinate to the executive branch – the American Artificial Intelligence Initiative) and aimed at the protection of national AI technologies. The project was developed directly by ministries, government research organizations and the NSA, DoD, IARPA, DARPA, etc. in 2016.
Cyber Technology in politics
Americans successfully use cyberstrategy to achieve their political goals. The most prominent examples are the American ambassador to Syria, Robert Ford, who contributed to the country’s destabilization through coordinated posts on Facebook, or the US ambassador Michael McFaul who put out numerous anti-Russian tweets and Youtube-videos.
In the US, a Hillary Clinton SuperPac with a budget of over a million dollars worked to “Correct the record” on the candidate, paying for trolls on social networks to work against her opponents. At the same time, Twitter and Google (like the mainstream media) openly worked to fix the competition for Clinton.
Trump’s SuperPAC made its own efforts via the Great America Pac project. However, Trump’s main focus group was already right wing-oriented people.
The name has changed, but the essence remains the same – and there is no information about what algorithms they use for their own business. Is it ethical? Transparent? Who controls them? Nobody knows.
The Dark kingdom of Facebook
In 2011, Israeli intelligence agencies managed to prevent dozens of European pro-Palestinian activists from flying to Israel as part of the “Welcome to the Palestine” initiative, collecting information from open sources on social networks such as Facebook.
Another example is the mobilization in Colombia through a group on Facebook called “One Million Voices against FARC” in 2008, where rallies were organized that gathered hundreds of thousands of people in Latin America. Interestingly, at that time, Facebook was not as popular in this region as it is now, and the question is, who promoted the messages in general and what target groups were there during the campaign?

In 2011, the CIA confirmed that mass protests in Iran in 2009, known as the Green Revolution, were tied to Twitter, and prompted the CIA to begin systematic monitoring of social networks on the Internet. Protests of the “Arab Spring” and Taksim square (Gezi park) protests in Turkey were also fermented artificially on social networks, especially on Facebook.
Facebook has long been used as a cyber-weapon. In 2012, there was a scandal involving the US and France after the discovery of a complex virus inside the computer system of the Presidential Palace. Sources from the French Network and Information Security Agency (ANSSI) claim that this attack, which occurred shortly before the presidential election, was made by the United States (curiously, US National Security Secretary Janet Napolitano refused to confirm or deny the US allegations of involvement in the alleged hacking!). The investigation revealed that the alleged virus was originally sent to employees of the Palace of the Champs Elysees via Facebook (the attackers acted worked via fake accounts).
Since 2016, US authorities have strengthened cooperation with Facebook, when the State Department organized the initiative “The P2P (Peer to Peer): Challenging Extremism initiative.” Formally, the talk was about the partnership of the US authorities with universities, with interesting internships and the development of digital products against extremism. Facebook joined the program and sponsored three additional university teams to Washington, DC to participate in the second contest, the Facebook Global Digital Challenge.
The Kurds
It is also interesting to see how Facebook’s policies have changed for Kurds who use the platform to promote their own agenda. In 2013, Kurdish Rudaw, located in Erbil (Iraq), confirmed that Facebook censored the content of Kurdish groups, especially content that supports the Kurdistan Workers Party (PKK), which is recognized as a terrorist organization in many countries.
But the protest came not only from Iraq. Western media also launched a campaign in support of Kurdish political groups. Here, for example, the statement of Facebook’s European office, published in Deutsche Welle:
“The BDP page was not removed for mentioning the word ‘Kurdistan’. It is true that several BDP pages have been taken down from Facebook. This is because these pages have repeatedly breached Facebook’s rules. These rules allow users of Facebook to post political content, including controversial views, but prohibit the posting of content that shows support for internationally-recognised illegal terrorist organisations [including the PKK].”
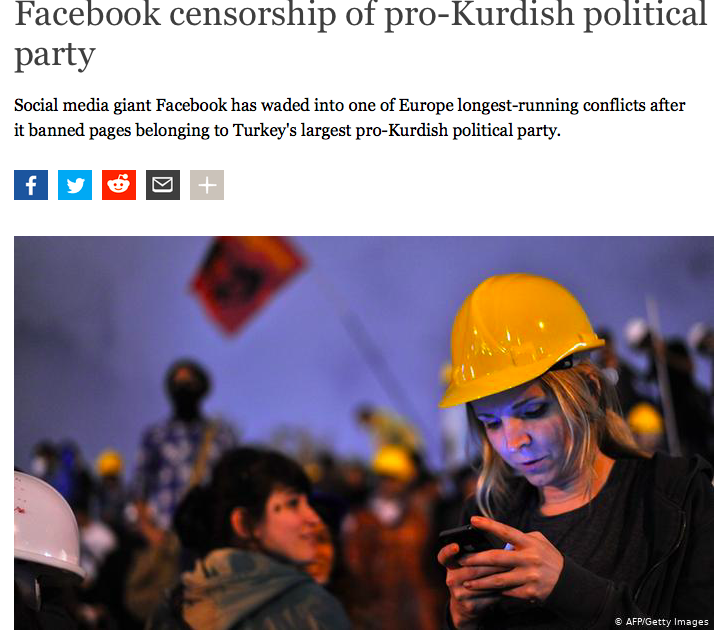
At this time, Facebook followed certain standards of abuse, but then the rules were changed. The Kurdish page was restored in 2016. It should be noted that the phone number on the page is from the UK.
While some groups still indicate the countries from where they are administered (such as Kurdistan24 (Erbil, Iraq), with others it is completely incomprehensible who is behind them.
But many groups are moderated by individuals living in European countries, the USA and Canada. For example, administrators of Independent Kurdistan are from Romania, Canada and the UK.
Sometimes administration is mixed (domestic and foreign), as on the page of the Democratic Party of Kurdistan.
Turkey
“Turkey has been accused of violating academic freedom by rounding up university teachers who signed a petition denouncing military operations against Kurds in the south-east of the country,” the Guardian wrote, noting how the West launched a campaign of pressure on the Turkish government. On this occasion, the US ambassador intervened himself.
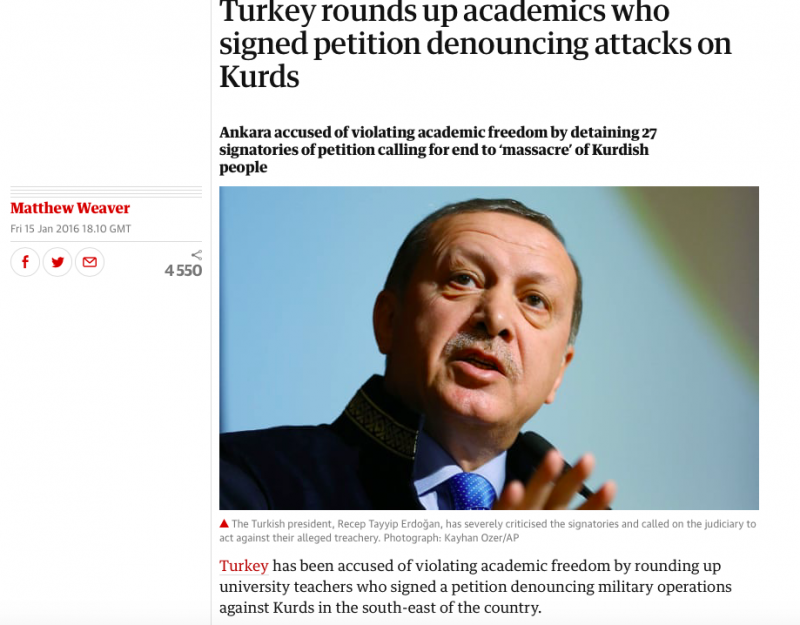
It is interesting, that this campaign was conducted in January 2016, and that a new page was created on January 30, 2016.
Finally, after the attempted coup in Turkey in July 2016, when it became clear that some Western agents (including Fethullah Gulen) were behind it, more pro-Kurdish accounts appeared on Facebook.
Other cases
A few years ago, India refused to accept Facebook’s “free basic” internet offer over fears of the company establishing a monopoly, but what about other countries in Africa, Asia and Latin America? Facebook’s predatory digital capitalism cannot be stopped based solely on the Indian precedent, and many nation states are not aware of the consequences of such a high level of infiltration.

Public Domain Pictures
Another prominent issue is that of professional trolling. The “war against trolls” declared by Facebook and the State Department, especially the external ones. While North Korean, Chinese, Iranian, Syrian, Russian and Venezuelan trolls all exist, this is only one side of the coin. Troll-culture was born in the USA, it is derived from American society itself. Secondly, if US government agencies and their proxies use the trolling methodology and distribute fake news with political intentions, it will be revealed and confirmed sooner or later.
Thirdly, the atmosphere which pushes people into trolling remains. Whitney Phillips believes that trolls fit very well into the modern landscape of multimedia digital media. According to her, their behavior is often in direct accordance with the actions of social network marketers and the interests of large corporations.
Conclusion
It is clear that the United States is attempting to maintain global governance through surveillance and control methods online. Social networks and passion for IT / gadgets are a tool for manipulating people (both domestically and abroad). The model of observation and control was imposed on the international community through extreme neoliberal ideology, free markets, a globalized economy and the growth of the information society. Because nation-states are finding it increasingly difficult to respond to social needs at the same time their voices are being crowded out by money and first-world technology, the axis pushing a transhuman future predicted by modern electronic devices and applications continues to grow in strength. People are becoming a prosthesis of the artificial world and the object of networks and systems: citizens are more and more victims of a perverted vision of reality, caught up in defending their rights and their will to rebel. Facebook remains one of the main players pushing this agenda, a strategy most predominantly championed by the US’ hegemonic apparatus.

















Leave a Reply